About the Course
““Ethical hacking is like a double-edged sword – it can be used for protection or destruction. The choice lies in the hands of the wielder.”
― Ankit Fadia, Ethical Hacker and Author
Our Ethical Hacking and Cybersecurity course is designed to help you understand the basics of this ever needed IT skill. Led by experienced teachers, you’ll have the opportunity to practice what you’ve learned through hands-on exercises. This practical approach will prepare you for well-paying jobs in a variety of industries where cybersecurity is crucial.
In today’s digital world, companies are constantly seeking skilled professionals to protect their data and systems from cyber threats. By completing our course, you’ll gain the skills that employers are looking for, making you a valuable asset to any organization. Additionally, our certification serves as proof of your proficiency in cybersecurity, giving you a competitive edge in the job market.
Our course remains affordable, ensuring that it’s accessible to anyone interested in pursuing a career in this field. Furthermore, we assist with internship and job placement upon completion of the course, making the transition into the workforce smoother and more manageable. Join us today and embark on a rewarding journey towards a successful career in Ethical Hacking and Cybersecurity!
What You Will Learn
- Complete beginner-friendly Ethical Hacking course
- Learn basic Ethical Hacking techniques step-by-step
- Gain fundamental knowledge in Cyber Security
- Understand basic concepts of Information Security
- Explore essential Networking basics for Ethical Hacking
- Learn about Password Cracking and Browser Security
- Discover common security risks in wireless networks
- Secure basic operating systems like Windows, Mac OS, and Linux
- Understand basic legal and ethical considerations in Ethical Hacking
Ethical Hacking Course Details - Modules
- What is a Computer Network?
- Basics of Communication Systems
- LAN, MAN and WAN
- Transmission Media, OSI and TCP/IP stack
- Internet Protocol
- TCP/IP Applications
- Security Principles
- Vulnerability
- Security Threats and Attacks
- Social Engineering
- Physical Security
- Steganography
- What is Kali Linux
- Importance and Scope
- Kali Linux Installation
- Kali Linux Tools
- What is Hacking
- What is Ethical Hacking
- What is Cyber Security
- What is Penetration Testing
- Risk Identification
- Risk Analysis
- Risk Mitigation Strategies
- Risk Monitoring and Management
- What is Network scanning
- Types of Scanners
- Nmap
- OS Detection
- Nmap – Scripts & Script Engine
- Nmap troubleshooting
- Introduction to Footprinting
- Information Gathering
- Footprinting Techniques
- Footprinting Website & Tools
- Basics of Cryptography
- Evolution & Data Encryption Methods
- Types of Cryptography
- Private & Public Key Exchange
- Secret key Cryptography
- Message Authentication and Hash Function
- Digital Signatures and Public Key Infrastructure
- What is Proxy Server
- Types of Proxies
- Benefits of Proxy
- What is a web server
- Types of web attacks
- What is Phishing
- Phishing Techniques
- Phishing Tools
- What is Malware
- Types of Malware
- Malware Tools
- Unauthorized Application Execution
- TCP/IP Packet Formats and Ports
- Firewall and IDS
- Switch Attacks
- Router Attacks
- DoS, DDoS, Session Hijacking
- Advanced Techniques
- Session Hijacking
- What is System Hacking
- What is Password Cracking
- Vulnerabilities & Countermeasures
- Spyware, Rootkit, Steganography, Trojans
- Computer Worm, Backdoor, Buffer Overflow
- Linux Basics
- Linux Threats
- Linux Security
- Kernel Patching
- What is a sniffer
- Sniffer Functions
- Sniffing Techniques
- Sniffing Tools
- Introduction to Proactive Defense
- Threat Intelligence and Analysis
- Security Automation and Orchestration
- Emerging Threats and Trends in Proactive Defense
- What is Security?
- Layer 1 Security
- Layer 2 Security
- Layer 3 Security
- What is VPNs
- Type of VPNs
- GRE
- IPSEC
- SSL
- What is an Intrusion Detection System?
- What is an Intrusion Prevention System?
- Configuring Intrusion Prevention System
- SIEM
- What is SIEM
- Incident Response
- What is Incident Response
- Cloud Computing and Security
- Identity Access Management
- Security Policies
- Mobile Security
- New Threats
- Classification of cybercrimes
- Cybercriminals modus operandi
- Reporting of cyber crimes
- Cyber Laws and Policies
- IT Act 200, IPC and Copyright Act
- Security issues related to social media, Email policy
- Cybercrime and Cyber security Organisations in India
- Case studies
Tools to Master
Network Scanning Tools
Advanced IP Scanner
Angry IP Scanner
Fping
Nessus
Netcat
NetScanTools
Nmap
Unicornscan
Vulnerability Scanning Tools
Acunetix
GFI LanGuard
Nexpose
Nikto
OpenVAS
Qualys
SAINT Security Suite
Burp Suite
Password Cracking Tools
Aircrack-ng
Hashcat
Hydra
John the Ripper
L0phtCrack
Medusa
RainbowCrack
Ophcrack
Exploitation Tools
Armitage
BeEF
Canvas
Core Impact
Metasploit
SET
SQLMap
SQLMap
Packet Sniffing and Spoofing Tools
Bettercap
Ettercap
Hping3
NetworkMiner
Responder
Snort
tcpdump
Wireshark
Wireless Hacking Tools
Bettercap
CoWPAtty
Crunch
Fern Wi-Fi Cracker
InSSIDer
Kismet
Reaver
Wifite
Web Application Hacking Tools
IronWASP
Ratproxy
Shodan
Skipfish
Vega
Wapiti
WebScarab
W3af
Forensic Tools
Autopsy
CAINE
Dumpzilla
Foremost
Scalpel
SIFT
The Sleuth Kit
Volatility
Social Engineering Tools
Evilginx
Ghost Phisher
GoPhish
King Phisher
Maltego
MSFPC
Wifiphisher
SET
Certificate Awarded
By successfully completing the course and required projects you will receive an industry-recognized Completion Certificate in Ethical Hacking and Cyber Security. The Certificate will help you in your Career Advancement and open doors to endless Opportunities.
Top Hiring Companies
Cyber Security Trends
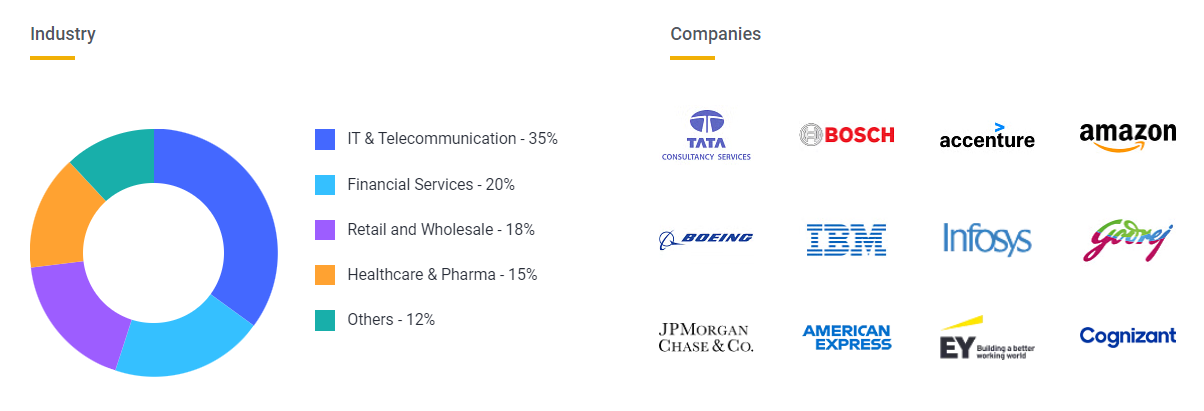
The global cybersecurity market size stood at USD 172.32 billion in 2023 and is projected to reach USD 424.97 billion by 2030, registering a CAGR of 13.8% during the forecast period 2023-2030.
$345 billion
Market Growth By 2026
Source: Glassdoor
13.8% CAGR
Between 2023 and 2030
Source: Business Fortune
308 K
Available Jobs
Source: LinkedIn
₹11-12 L
Average Annual Salary
Source: Glassdoor
Career Opportunities
- Cyber Defense Analyst
- Cybersecurity Analyst L1,L2,L3
- Cybersecurity Auditor
- Cybersecurity Consultant
- Information Security Analyst 1
- Information Security Manager
- Infosec Security Administrator
- IT Security Administrator
- Senior Security Consultant
- Mid-Level Information Security Auditor
- Network Engineer
- Network Security Engineer
- Security Administrator
- Security Analyst
- Security Analyst L1
- Senior SOC Analyst
- SOC Security Analyst
- Solution Architect
- Warning Analyst
- Vulnerability Assessment Analyst
Why start your Ethical Hacking and Cyber Security journey with Ties Infotech
Ties Infotech is a leading IT Training and Placement Institute with proven track record. Benefit from the guidance of our experienced and knowledgeable instructors who are well-versed in the field of ethical hacking, ensuring a high-quality learning experience. Receive targeted guidance and resources to prepare for the Certified Ethical Hacker (CEH) exam, increasing your chances of success.
By choosing Ties Infotech, you are investing in your future and ensuring that you will have the skills and knowledge needed to excel in the fast-paced and constantly evolving field of cybersecurity.
- Practical Training
- Personal Attention
- Live Demo Classes
- Live Projects
- Part Time Courses
- Free Training on Linux
- Hands-on lab Exercises
- Paid Intership in MNCs
- Expert Industry Trainers
- 20+ years of Experience
- Foolproof Career Guidance
- Affordable Competitive Fees
- 100% Placement Track Record
- Centrally Located in Deccan, Pune
- Coaching in English, Marathi and Hindi
- Flexible Regular and Weekend Batches
- Learn from scratch for Beginners to Advanced
- Guidance for Global Certification Exams
- Practice for International/Global Certification
- Repeat Sessions on request
Become a Professional Ethical Hacker and Safeguard the Digital World
- Security Analyst
- Warning Analyst
- Solution Architect
- Network Engineer
- Security Analyst L1
- Senior SOC Analyst
- Cybersecurity Auditor
- SOC Security Analyst
- Security Administrator
- Cyber Defense Analyst
- Compliance Officer
- Cryptographer
- Forensic Analyst
- Forensic Investigator
- Malware Analyst
- Penetration Tester
- Cyber Security Consultant
- IT Security Administrator
- Cybersecurity Consultant
- Senior Security Consultant
- Network Security Engineer
- Ethical Hacking Trainer
- Information Security Manager
- Infosec Security Administrator
- Information Security Analyst
- Vulnerability Assessment Analyst
- Mid-Level Information Security Auditor
- Cybersecurity Analyst L1, L2, L3
- Cloud Security Analyst/Architect
- Computer Forensic Analyst
- Threat Intelligence Analyst
- Security Engineer/Architect
- Network Security Analyst
- Threat Researcher Incident Responder
Ou Alumni Work at























Have Queries. Contact us Now!
Placements